Single Sign-On (SSO) Authentication
Important
Information and features vary according to the roles to which you belong and the permissions associated with those roles. For more information, contact your module manager or your campus support team.
Jenzabar supports single sign-on (SSO) for J1 Web and JICS, which lets users securely access multiple websites in your campus computing environment without having to log in separately to each. This eliminates the need for users to remember multiple passwords and once logged in, lets them switch between campus web resources.
J1 Web follows the SAML 2.0 standard and operates as a service provider in a SAML 2.0 environment.
“SAML 2.0 is an XML-based protocol that uses security tokens containing assertions to pass information about a principal (usually an end user) between a SAML authority, named an Identity Provider, and a SAML consumer, named a Service Provider.” (Wikipedia Contributors. “SAML 2.0.” Wikipedia. Wikipedia.org, 16 January 2019, en.wikipedia.org/wiki/SAML_2.0. Web. Accessed 28 June 2019.)
In the Jenzabar SSO environment, users are authenticated via web browser redirection. If the user is not authenticated in J1 Web, the web browser is redirected to a login page from the SSO identity provider. Once a user is authenticated via the SSO provider’s site (e.g To., by entering a valid name/password, following a biometric process, etc.), the web browser redirects back to J1 Web and the user is successfully logged in. The scenario may change when JICS is involved, or if the user already has SSO authentication. Without SSO, there are separate sign in pages and sign out procedures. With SSO, the sign in and out pages and procedures are more streamlined. Depending on how your school sets up SSO, session timeout processes may use a single launch page and /or related sign in page to manage access. For example, users might be directed to the launch page or immediately redirected to J1 Web or JICS.
When are the sign in and launch page accessible to users?
When your school links directly to the launch page. When the user enters or clicks the direct link, they are directed to the sign in page. Once their credentials are verified, they see the launch page where they have quick access to J1 Web and JICS.
When a user accesses J1 Web using the base J1 Web URL or a specific J1 Web page (via bookmark, email link, desktop shortcut, etc.) and the SSO session has not yet been established. Typically users are immediately routed to the J1 Web or JICS page, but if the session isn’t established, they see the sign in page first.
When the user selects sign out from J1 Web, they are routed to the launch page where they can complete the sign out process.
When the user’s session times out, they are routed to the sign in page. Once they sign in, they can see the launch page where they can regain access to J1 Web and JICS.
To enable SSO, you must:
Set Up the SSO Application in Azure
Assign AD Users to the J1 Web Instance in Azure
Turn on SSO in Azure
Enable SSO in J1 Web
Test
Notify End Users
Important
Using J1 Web with Azure SSO currently requires an Azure Premium account.
Note
JICS configurations may impact how you establish your configurations. Some schools may need to have a separate configuration for every application to be authenticated.
Note
Screenshots in this document may vary based on the applications you’re authenticating via Security Assertion Markup Language (SAML).
Access http://portal.azure.com.
Log in using your Microsoft credentials. The Azure services page appears.
From the left pane, click Azure Active Directory.
The Overview page for your Active Directory domain appears.
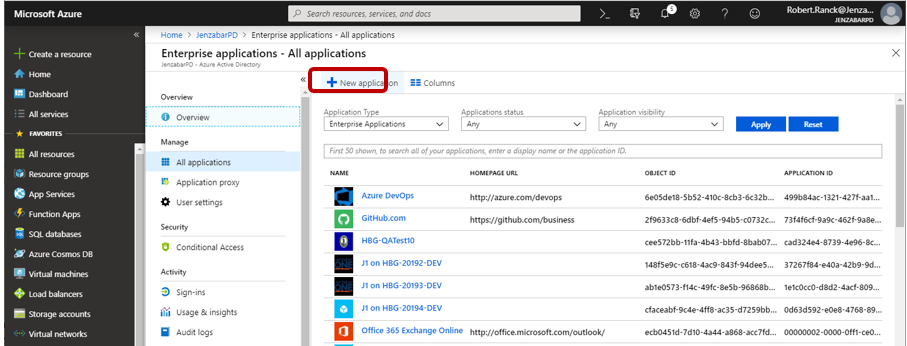
Click Enterprise applications.
The Enterprise applications – All applications page appears.
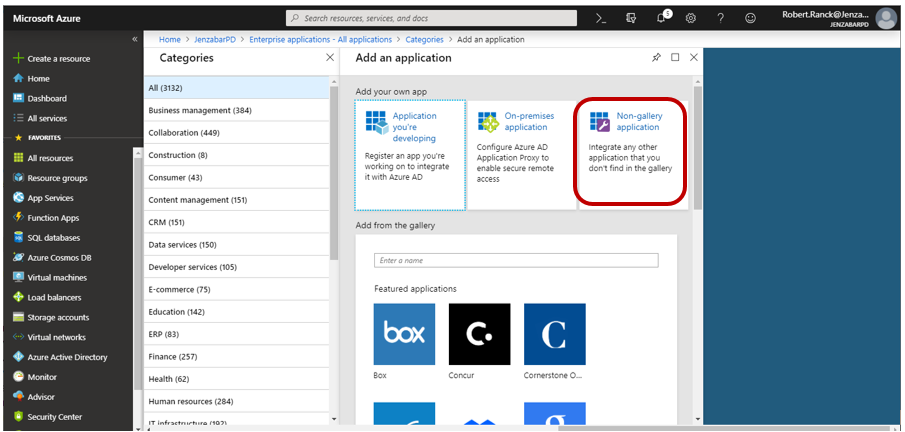
Click New application.
The Add an application page appears.
Click Non-gallery application.
Note
The Non-gallery application option is only available with a Premium account.
The Add your own application page appears.
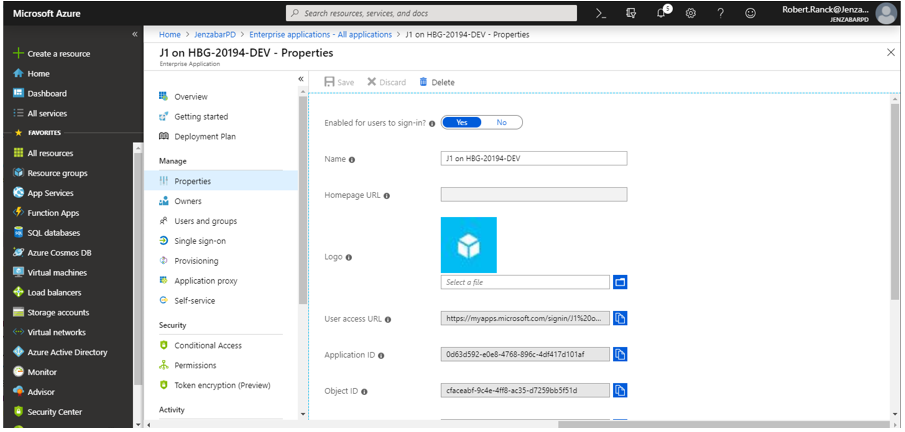
Move Enabled for users to sign-in? to No.
Note
Once setup is complete, this option is moved to Yes. More information will be included later on in the process.
In the Name field, enter the application name you want displayed to users when they sign in via SSO.
Note
You may need to set up two applications: one for your play/testing environment and another for your live/production environment.
Use the Logo field to upload an icon or logo image that will appear on the launch page and within the Azure environment.
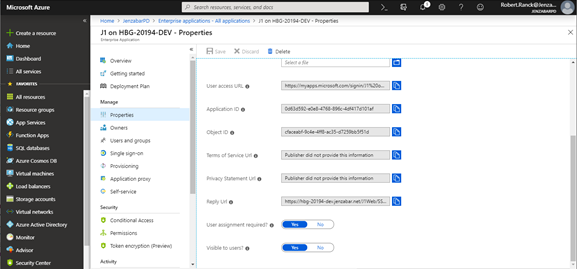
User assignment required? and Visible to users? configurations are optional. Read Azure’s online help tips available from the ? icons to guide your decisions.
Tip
User assignment required? allows users in active directory to see Jenzabar on the Azure page. For these steps, this option is moved to No. Once setup is complete, this option is moved to Yes.
Visible to users? determines if users will show up on the launch page or if they must know the URL.
Click the Add button at the bottom of the page. The Enterprise applications – All applications page appears showing your newly added application.
Select the application you just added.
From the left-hand side, click Single sign-on. The Select a single sign-on method page appears.
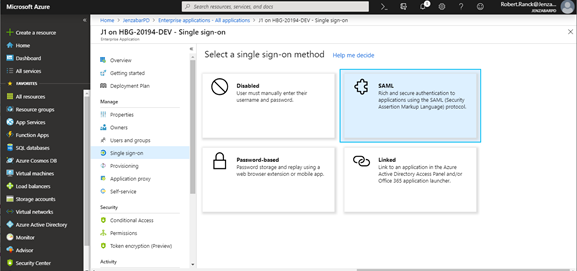
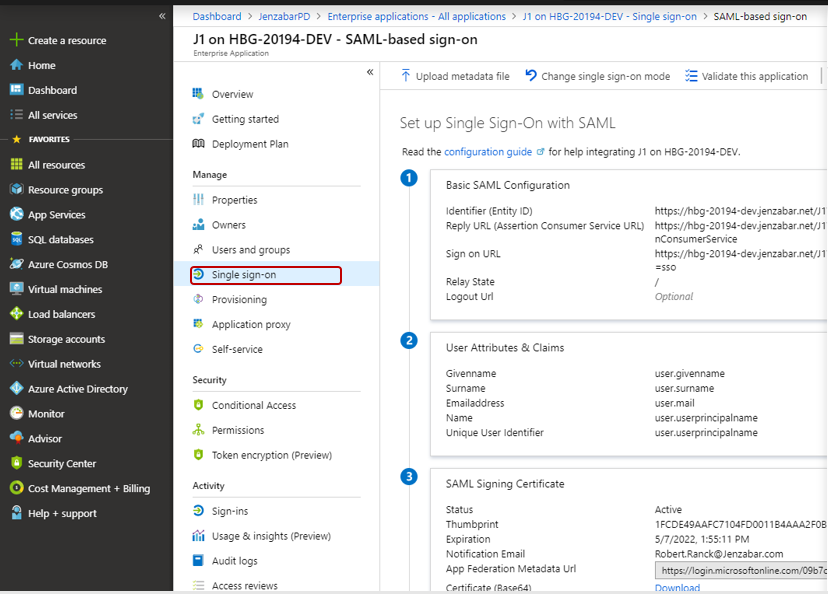
Click SAML. The SAML-based sign-on page appears.
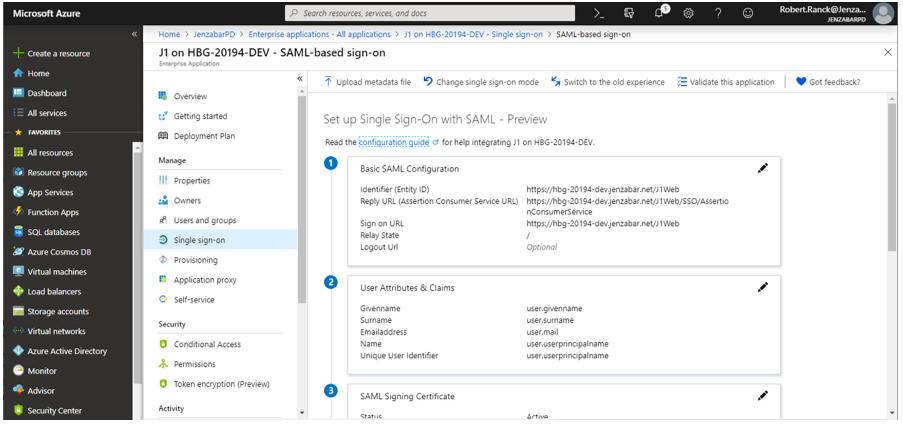
From the Basic SAML Configuration section, click the pencil Edit icon. The Basic SAML Configuration pop-up window appears.
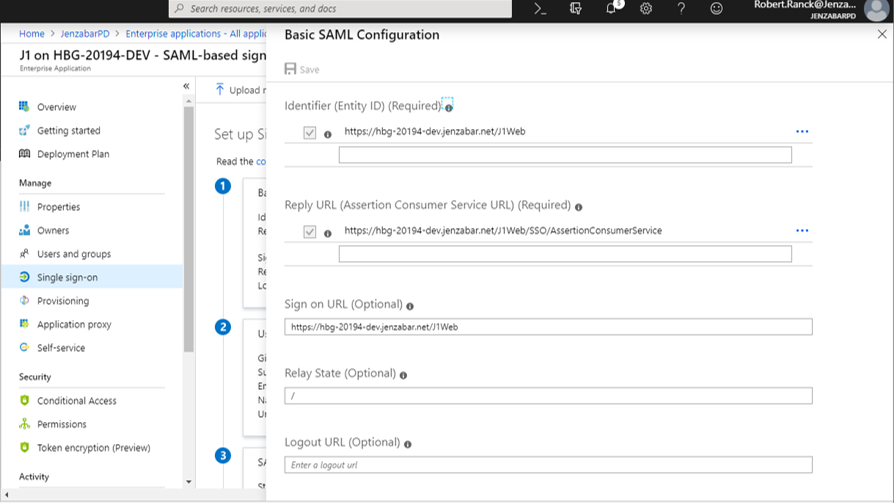
In the Identifier (Entity ID) field, enter your service provider name. This is the unique name used to identify the J1 Web site and how Azure will communicate with J1 Web.
Note
A website’s base URL can serve the unique identifier, but you aren’t required to use it. Just be sure it is spelled, capitalized, and punctuated exactly the same as it will be entered when configuring SSO in J1 later in this process.
Note how you entered the Identifier (Entity ID) name as it is entered later in J1 Web. Characters are case sensitive.
In the Reply URL field, enter a URL made up of the base J1 Web URL followed by /SSO/AssertionConsumerService. This URL is not visible to users.
Tip
https://myschoolname.net/J1Web/SSO/AssertionConsumerService
In the Sign on URL field, enter the J1 Web URL that will be visible to users. This is typically your current J1 Web site URL. For example, https://myschoolname.net/J1Web.
Click the Save button.
Click the x icon in the upper right-hand corner. The Basic SAML Configuration pop-up window closes and the SAML-based sign-on page reappears.
From the SAML Signing Certificate section, click the pencil Edit icon.
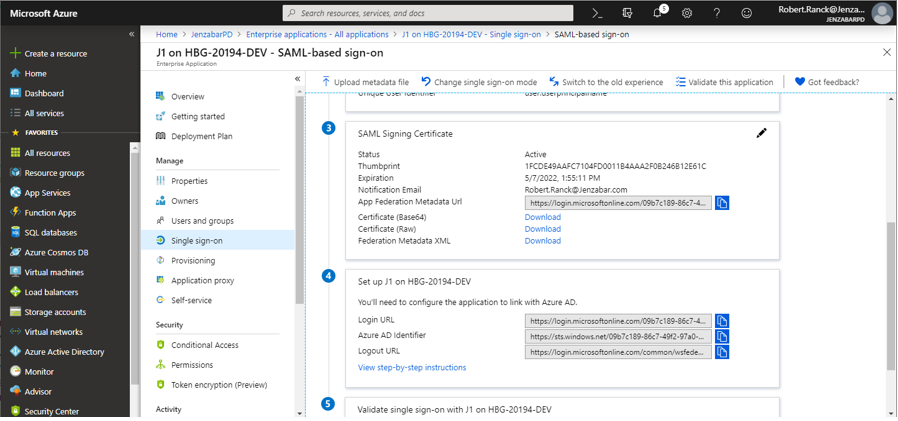
From the signing options, Jenzabar recommends selecting the following:
From the Signing Option drop-down, select Sign SAML assertion
From the Signing Algorithm options, select SHA-256
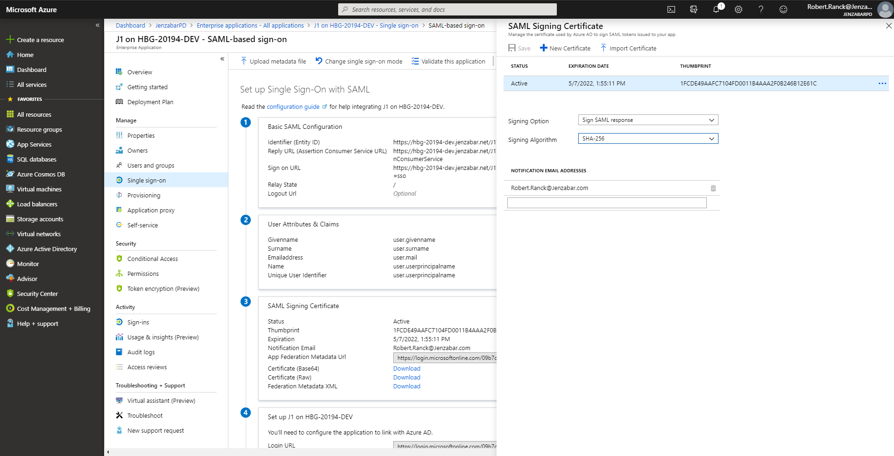
Click the x icon in the upper right-hand corner. The SAML Signing Certificate pop-up window closes and the SAML-based sign-on page reappears.
Access the J1 Web server Jenzabar program files and create a Certificates folder.
Tip
For example, C:\Program Files (x86)\Jenzabar\Certificates
Return to the Azure environment.
Click the Download link next to Certificate (Base64).
Note
Downloading steps vary according to your browser.
Locate the downloaded certificate and copy it to the Certificates folder created in Step 29.
Grant read and execute permissions to the Certificates folder and certificate. These permissions should be granted to the users in the app pool your J1 Website uses (e.g., Jenzabar_AppPool).
Note
This certificate is uploaded into J1 Web in Step 4: Enable SSO in J1 Web.
Access http://portal.azure.com.
Log in using your Microsoft credentials. The Azure services page appears.
From the left pane, click Azure Active Directory.
The Overview page for your Active Directory domain appears.
Click Enterprise applications. The Enterprise applications – All applications page appears.
Click on the J1 Web instance you defined.
Click Users and Groups.
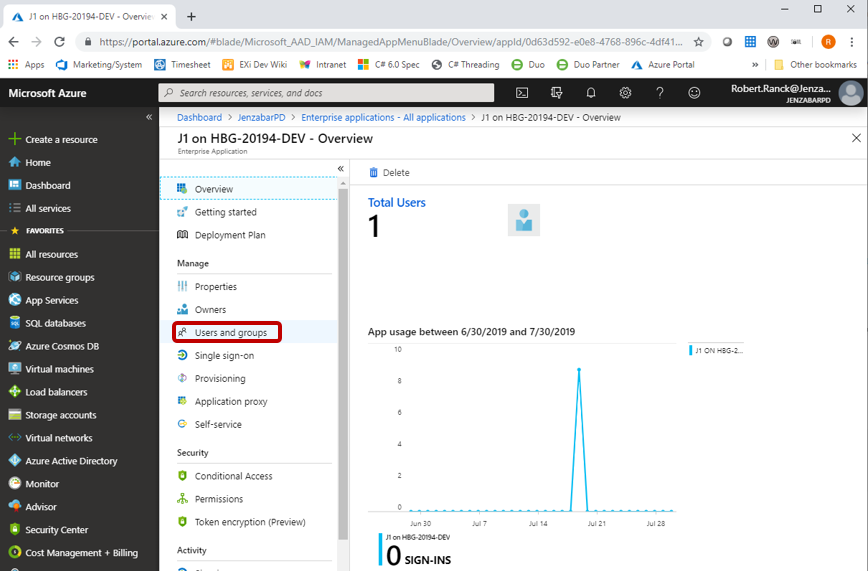
Use this page to associate your school’s Active Directory groups or individual users you want to be able to access J1 Web via SSO.
Access http://portal.azure.com.
Log in using your Microsoft credentials. The Azure services page appears.
Select your SSO application.
Click Properties.
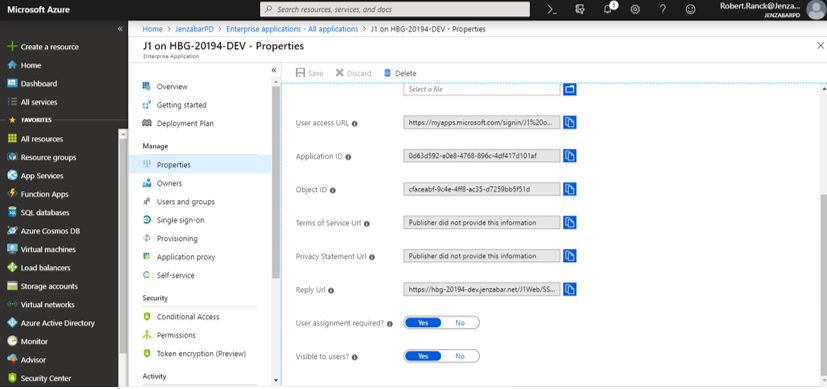
Move User assignment required? to Yes.
Move Visible to users? to Yes.
Click Save.
Important
Once SSO is designated the J1 Web Sign In Method, it is immediately implemented and domain options are unavailable.
Please reference the JICS documentation for steps on how to set up your Campus Portal to work with an identity provider (JICS 9.3.x Administration Guide available on MyJenzabar).
Notice
You can assign an AD Group to your J1 users in Desktop as a convenient way of assigning users to J1 Web SSO.
Log in to J1 Web as a user with System Administration Manager permissions.
Access the System Administration hub.
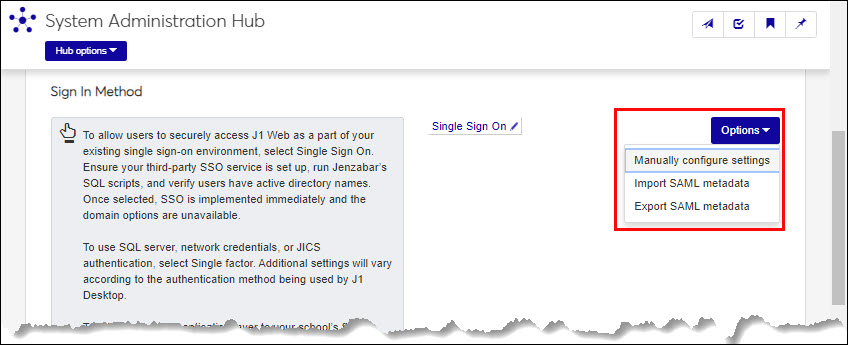
From the Hub options, select Product Installs and Sign In. The Product Installs and Sign In page appears.
Access the Sign In Method options.
From the Sign In Method options, select Single Sign On and click Save. The Options button appears.
Click Options.
To import SAML communication settings and relevant URLs from an XML file, select Import SAML metadata and follow the steps below.
Note
Before using the import process, access your identity provider and export the communication settings.
From the Open window, browse to the location where the SAML metadata XML file is located and select it. Note: This window may vary depending on the browser you are using.
Click Open. The Open window closes and the identity provider’s SAML communication settings, IP identifier, SSO, and launch page URLs are entered in J1 Web.
Tip
To view the imported information, select Manually configure settings from the Options drop-down.
To enter SAML communication settings and relevant URLs, select Manually configure settings. The Single Sign On window appears.
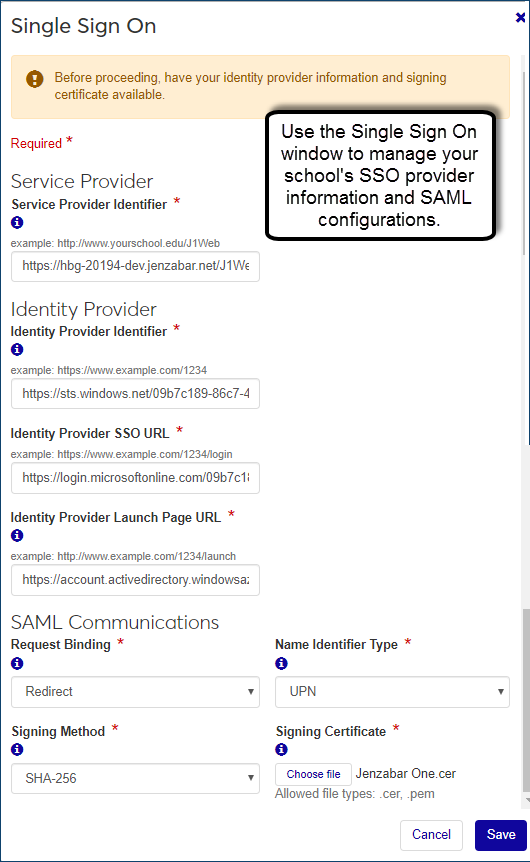
In the Service Provider Identifier field, enter the name you want to use to identify your J1 Web site in the SSO environment. This serves as the name your users will see in the SSO environment. This entry must match Step 20 in the "Set Up the SSO Application in Azure" section.
In the Identity Provider Identifier field, enter your identity provider’s name/identifier information. This establishes the identity provider and is commonly the identity prover’s base URL. You can copy and paste the Azure AD Identifier from the Azure portal Set up section.
In the Identity Provider SSO URL field, enter the URL your identity provider generated for redirecting J1 Web users. Logged in users are authenticated and redirected to J1 Web. Users that are not logged in are redirected to a sign in page.
In the Identity Provider Launch Page URL field, enter the URL your identity provider generated to appear when users sign out of J1 Web.
From the Request Binding drop-down, select Post.
From the Name Identifier Type drop-down, select the type of SAML response that will be used to identify the authenticated user.
If your school uses processes that synchronize the J1 NameMaster ID_NUM value into the AD employeeId, select J1 ID Number.
If your school does not use processes that synchronize the J1 NameMaster ID_NUM value into the AD employeeId, select UPN. The AD Sync or other similar process is used to populate the APP_USER DIRECTORY_SERVICE_USERNAME with the userPrincipalName values.
From the Signing Method drop-down, select the hashing algorithm that will be used to sign responses. Jenzabar recommends SHA-256. TIP: This must match the Azure configuration in "Step 1: Set Up the SSO Application in Azure," Step 27.
Upload your Signing Certificate by clicking Choose file. This certificate validates signed information from the identity provider. Note: This is the certificate downloaded in Step 31 of the "Set Up the SSO Application in Azure" section.
Click Save. The configurations are established and the login method is updated immediately.
Attempt to access your J1 Web environment with the following appended: ?ssoOverride=sso.
If the environment is configured correctly, you will be redirected to the SSO identity provider login page. If you are already logged into the SSO environment in the current browser session, or if Azure is able to log you in based on the Windows environment, the login page will be bypassed and you can proceed to the next step.
Login using the appropriate AD credentials. If the logged-in J1 Web page appears, then the full SSO process was successful.
If an error page appears indicating there is a problem logging the user in, then the SSO communications likely succeeded, but there is an issue with the user’s configuration in J1 Web. To troubleshoot, verify the following on the Desktop Users window:
User information in the Active Directory column (Desktop Users window) is accurate
Active Web Login checkbox is selected for the user
Notifying your end users about the new SSO feature and changes in your school’s new sign and out processes helps eliminate questions. The following outlines information you may want to share with your users, but this is high-level information varies according to your school’s implementation.
Share information about the new sign in page to be used to verify their credentials
Detail how they sign in (e.g., bookmark, link, shortcut, link to the launch page, etc.) impacts whether or not they see the J1 Web or Campus Portal page they want to access or the new launch page where they can then access J1 Web and the Campus Portal
Describe the sign out process. Let users know the only completely reliable way to close down an SSO environment is to close the browser
SSO increases online security as users commonly use similar or identical passwords for J1 Web and JICS, which means both accounts are compromised if one of them is subject to a security breach. The SAML protocol allows for SSO communications that are not signed with a certificate. This approach is not secure, but SSO is secure when appropriate signing is turned on (as done in these instructions).
If the user receives a J1 Web or JICS login error message, you know the issue isn’t with the identity provider. Use standard J1 Web and JICS login troubleshooting techniques. If the log in issue is with the identity provider, review the login history. For additional help with login issues, contact the Jenzabar Services Team.
Browser requirements will vary according to your school’s identity provider. For a full list of Jenzabar J1 Web supported devices, please see the Jenzabar Device Support Statement (https://www.myjenzabar.net/ICS/icsfs/Jenzabar_Device_Support_Statement.pdf?target=0e84ef50-0944-4ee1-b02a-0c5f16169406) on MyJenzabar.
Usernames and passwords are still managed in your school’s active directory server.
They can log in to each role using separate user IDs and passwords, based on their current access as a staff or student accordingly.
If JICS and J1 Web use the same SSO provider and they tell the provider to log out, yes. Once a user logs out of the identity provider, JICS and J1 Web time out on their own (according to how a school sets them up).
From the Options drop-down, select Manually configure settings. You can see the communication information and URLs on the Single Sign On window that appears.
When you import SAML metadata, any identity provider information that already existed in the system is replaced by the information in the new XML file.
Verify the metadata file you're importing is in an XML format.
Verify your identity provider exports into the SAML metadata format.